Revisiting Web 2.0
The Web 2.0 term has now been widely accepted as a description of a new pattern of ways the Web is being used. We have progressed from the publishing paradigm which characterised what is now sometimes referred to as Web 1.0, in which small numbers of content creators made use of tools ranging from desktop HTML authoring tools through to enterprise Content Management Systems and corresponding editorial and quality assurance processes to produce content for passive consumption by end users. In a Web 2.0 environment, large numbers of users are creating content using a seemingly ever-increasing variety of tools and devices with such content being made available via a wide variety of commercial Web 2.0 services.
The characteristics of Web 2.0 were described by O’Reilly (2005). The key areas relevant to this paper include:
- Application areas, including blogs and wikis, social sharing services and social networking services;
- The ease of reuse of content elsewhere through syndication formats such as RSS and Atom and other embedding technologies;
- A culture of openness and sharing which has been helped through the development of copyright licences such as Creative Commons;
- The concept of the ‘network as the platform’ by which services are hosted on externally-hosted services and accessible over the network, rather than a managed service within the organisation.
Although the value of the Web 2.0 term has been questioned by some, it does provide a useful way of defining a new phase in the evolution of the Web.
Use of Web 2.0 by Museums
Use of Web 2.0 at Brooklyn Museum
Caruth & Berstein (2007) provided insight into the ways an early adopter made use of a variety of social networking services. The paper described how Brooklyn Museum used services “involving but not limited to Blogger, Flickr, MySpace, Facebook, Blip.tv, YouTube, Cell Phone Audio Tours, and podcasts/mp3 downloads” to support the aims of their museum.
A follow-up paper (Bernstein, 2008) described further developments at Brooklyn Museum, including further project work and development. This work included the development of the Artshare Facebook application which allows Facebook users to select from the Brooklyn Museum collection works of art which they can shuffle on their personal profiles. This application was subsequently developed further to allow other museums to use it to share works in their own collections, allowing artists on Facebook to upload their own artwork to share with friends.
The Museum Blogosphere
Chan & Spadaccini (2007) have documented the growth of use of blogs in museums: “as 2006 began, there were less than thirty known museum blogs; since then, that number has more than doubled”. The paper went on to state that in 2007 “there are well over 100 blogs exploring museum issues, from a range of institutions and individuals across the globe”. Museum Blogs (http://www.museumblogs.org/) is a directory of museum and museum-related blogs and aggregators which aims to raise awareness and increase the authority of sites focusing on museum issues. In January 2009 the directory contained a total of 286 museum-related blogs.
Use of Twitter by museums
A small number of early adopters at the Museums and the Web 2007 conference were using the Twitter micro-blogging service. By the following year, Twitter usage had grown across this sector, with the Onetag service providing an aggregation of Twitter posts (tweets) related to the conference (Ellis, 2008).
We are now seeing larger numbers of institutions (as opposed to individuals) using Twitter, including Brooklyn Museum (http://twitter.com/brooklynmuseum), the Getty Museum (http://twitter.com/GettyMuseum) and the Science Museum (http://twitter.com/sciencemuseum). Promotion of the use of Twitter by museums appears to have started in 2007, with a blog post on “What is Twitter, Really? And Can It Do Anything For Museums?” published in April 2007 (Simon, 2008a).
Following the initial take-up of Twitter we are now seeing advice which seeks to explain the potential benefits and best practices in its usage. The “An Open letter To Museums on Twitter” blog post (Simon, 2008b), for example, provides a list of suggestions; such as, “Don't use Twitter to spam me about visiting”, “It's okay if you start by just following,” “Once you decide to tweet, make it interesting,” and “Tell me something I can't find on your homepage”.
We can see a trend in which new services are initially used by individuals who are willing to make use of such innovations. Such services may then start to be used in an organisational context by the early adopters, helped by the advocacy activities of the users who like to share their experiences with their peers. We then start to see the development of advice on best practices. The next stage is likely to be the provision of directories – and here we find that a Twitter group of museum Twitter feeds has already been established (Twittergroups, nd).
Acceptance of the relevance of Web 2.0
There is no real need to expand further on the variety of ways museums have started to exploit the potential of Web 2.0. Case studies on the use of wikis, video services, podcasts, etc. have been widely published. For now, we should acknowledge that Web 2.0 is becoming mainstream in the sector. The challenge now is to revisit some of the concerns which were raised by skeptics, to explore whether such concerns are legitimate and, where they are, to develop approaches for addressing such concerns.
The Concerns
Identifying the concerns
UKOLN has delivered a series of workshops which aim to provide an understanding of the potential of Web 2.0 and also identify potential barriers to the effective deployment and use of such services and explore ways in which such barriers can be addressed. Feedback is available from several of these workshops (UKOLN, 2008a; UKOLN, 2008b). This information, provided by practitioners within the sector, has informed the ideas described in this paper.
Sustainability issues
Adie (2008) has pointed out that Web 2.0 services which rely on a global scale in terms of numbers of users and/or on social networks will become decreasingly useful if the number of users drops. Essentially, the network effect works both ways. He also referred to the University of Edinburgh Guidelines for Using External Web 2.0 Services (Edinburgh, 2007) and described the risks involved in the institution’s use of remote Web 2.0 services, especially in terms of compliance with the Data Protection Act.
Failures in the services provided by Web 2.0 companies are happening. Kelly (2008a) has described a personal example of this with the Squirl service for managing small collections. The service’s interface to Amazon seemed to fail, with no Amazon book record being retrieved from the service. Further investigation revealed, worryingly, that the service’s data export function was also broken, meaning that the data could not be easily exported from the service. In addition, Squirl’s fault-reporting e-mail address is no longer functional.
Such considerations need not, however, mean that organisations need to shy away from use of third-party services. If this were the case, then we would not entrust our savings to banks, but would keep the cash hidden under our mattresses. Rather, there is a need to evaluate the risks and to develop risk management strategies. Let us now explore some other types of risk.
Digital preservation
Are we in danger of living in the digital dark ages, as some have suggested, with Web-based resources disappearing as organisational policies and priorities change and technologies change?
A project on the Preservation of Web Resources (JISC PoWR) was funded by the JISC in order to explore more deeply the challenges faced by institutions and to provide recommendations and develop advice on best practices. The project made use of a blog (JIISC PoWR, 2008a) which highlighted various challenges of preservation in a Web 2.0 environment.
The Human Factors
It would be a mistake to regard the risks in providing services based on use of externally-hosted services as only concerned with the sustainability of the services themselves. There is a need to appreciate the risks associated with the human element. This might include the initial adopters and enthusiasts losing interest in services such as blogs and wikis, resulting in blogs no longer regularly updated, wikis not maintained, and inappropriate comments or automated comment spam not removed from services. The Museums Wiki (http://museums.wikia.com/), for example, was established in 2006 to provide a space for sharing resources and ideas about museums. However, based on pages on forthcoming events, changed pages, etc. it would appear that the service has not gained the momentum which was hoped for.
Accessibility issues
Many public sector organisations around the world will have both legal and ethical requirements to ensure that their resources and services can be accessed by people with disabilities. In the UK the DDA (Disability Discrimination Act) requires organisations to take reasonable measures to ensure that people with disabilities aren’t discriminated against unfairly. The Web Content Accessibility Guidelines (WCAG) developed by the W3C Web Accessibility Initiative (WAI) play an important role in documenting approaches which can help to ensure that Web resources can be rendered by Web browsers and assistive technologies for users with a range of disabilities.
It is sometimes felt that all Web resources must conform to WCAG guidelines, and that this requirement will rule out the deployment of many Web 2.0 services which may be dependent on technologies which are deprecated in the WAI guidelines. However, as Sloan (2006) describes, the WCAG 1.0 guidelines have significant limitations, including their reliance on browsers which conform to User Agent Accessibility Guidelines (UAAG) and authoring tools which conform with Authoring Tool Accessibility Guidelines (ATAG).
Exploiting the Potential of Web 2.0
We have reviewed some of the ways in which Web 2.0 services have grown in popularity over the past couple of years. We have also looked at examples of the concerns associated with such approaches. In this section we summarize some of the broad approaches which can help to ensure that institutions maximize the potential dividends which Web 2.0 seeks to provide.
Advocacy
Although awareness of Web 2.0 is widespread in many circles, there is still a need for advocacy of the benefits to be gained, especially with senior managers and organisations which may traditionally be resistant to change. Research interests and the need to engage with young people often help to ensure that higher education institutions are early adopters of innovations. However, in other sectors such drivers will be missing, and even in higher education there may be resistance to changes especially if the benefits of change to existing working practices are not obvious.
Within the UK, UKOLN has taken a high profile in promoting the benefits of Web 2.0 to a variety of communities, including higher education and the cultural heritage sector. Such advocacy activities have included presentations at national and regional events aimed at the cultural heritage sector (UKOLN, 2008c; UKOLN, 2008d ;UKOLN, 2008e; Kelly, 2008b).
Listening
Advocacy activities need to be complemented by listening activities which help to provide a better understanding of both specific requirements within organisations and the various concerns which may be expressed.
UKOLN has delivered a series of workshops aimed at museums, libraries and archives; they have used wikis as a mechanism both for gaining feedback on potential use of Web 2.0 services and for documenting concerns and barriers encountered or expected by practitioners in the sector. The UK Web Focus blog (http://ukwebfocus.wordpress.com/) provides both a dissemination and communications forum for discussion and debate on best practices of use of Web 2.0 services.
Case study: Amplified Conferences
This example of an ‘amplified conference’ (Wikipedia, 2008) reflects a growing trend at IT and e-learning conferences. We are also seeing awareness that the main challenges are not necessarily the technical ones but the human issues, including understanding the purposes the technologies are being used for, addressing the potential distractions that such technologies may cause, and facing the legal and ethical challenges related to issues such as data protection, privacy and social inclusion.
A debate on the potential distractions caused by use of networked technologies in a conference environment has been featured on the Ed Techie (Weller, 2008) and UK Web Focus blogs (Kelly, 2008c). The debate has parallels with discussions on changes in the physical space, from a quiet environment for individual reading to a social space for community activities. We are seeing developments of approaches which seek to address the concerns of the two camps, ranging from use of the physical space, with separate areas for those who wish to use their PCs and those who prefer a quieter environment, through to, perhaps, the development of hardware solutions which minimize noise made when typing.
The issues of data protection and privacy may be more complex to address. Many people are happy to be included in photographs and videos, and for these to be made available on-line. However, as Andy Powell has described (Powell, 2007), sometimes individuals may object to this, with the result thatsuch images are removed from public Web sites, and the effort of any associated processing of the resources has to be written off. It may be argued that an approach to addressing such matters may be based on human sensitivities to such issues and flexibility rather than blanket bans. However, the need for Acceptable Use Policies in such cases has been described (Kelly, 2005).
Preservation in a Web 2.0 environment
The JISC PoWR project published guidelines on advice for Web preservation, and included advice on use of Web 2.0 services. As described in the project’s final report (JISC PoWR, 2008b), a variety of approaches can be taken to address preservation challenges, including use of syndication technologies to replicate content at multiple locations.
The ease of content creation and the huge diversity of ways Web 2.0 services are being used can mean that the disposition of resources is more relevant than it was in an environment where the creation of digital data was a time-consuming and resource-intensive task. Organisations may well decide that the preservation of digital resources such as Twitter posts or Skype telephone calls and instant message chats is not required.
A culture of openness
The provision of training and staff development courses is supported by the availability of resources with Creative Common licences which allow for their reuse, perhaps for non-commercial use. There is a likelihood that Web 2.0 advocates will have embraced a culture of openness and have a willingness to allow their resources to be reused by others.UKOLN has recently released a number of briefing documents covering a variety of Web 2.0 areas which are available with a Creative Commons licence (UKOLN, 2008f) provided the aim is to maximize the organisation’s impact within the higher and further education and cultural heritage sectors. This decision also reflects an organizational culture of openness where slides used in many presentations have made use of Creative Commons licences, and access to the resources is maximised through use of popular sharing services such as Slideshare.
Risk Assessment and Risk Management
Risk assessment to support events
A risk assessment approach was developed at UKOLN, initially to support use of externally-hosted Web 2.0 services at a high profile annual UKOLN event, first in 2005 and more recently in 2008 (UKOLN, 2008g). The approach required a description of why the service is being used, a statement of the perceived risks, and details of how such risks are to be addressed, as summarized below:
Support UKOLN's Role: An important role is to keep abreast of emerging new technologies in order to provide advice on best practices to its stakeholder communities.
Advise Our Communities: Many institutions have an interest in Web 2.0, including technologies which provide social networking services and integration of content from diverse sources. Making use of such technologies allows us to provide effective advice, based on experience gained.
Provide Richer Experiences To Our Users: The hosted services aim to provide useful services to the target audience - participants at the event.
Minimise Resource Efforts: In order to minimise the use of scarce software development expertise, we use services which are freely available.
Provide A Test Bed: We seek to host appropriate services after the workshop in order to monitor changes to the services, such as withdrawal of or changes to the licence conditions, enhancements to the services, etc.
Gain Experience Prior To Service Deployment: Evaluation of the services can provide feedback on the merits of the services which will be valuable if the services are deployed more widely.
Maximise Impact: If the technologies prove significant, demonstration at the event provides an opportunity to maximise impact by exposure to 170 delegates.
Examples of possible risks and the risk assessment and risk management strategies taken were:
- Use of a 3rd party usage statistics service: a well-established service was used, with data being provided in any case on the Web service.
- Use of a video blog: there were risks that the data might not be extractable from the service. However, as the video related directly to specific aspects of the event, long-term management of the content was not deemed necessary.
- Use of del.icio.us to bookmark resources: del.icio.us is a well-established service. In case of problems it should be possible to make use of del.icio.us APIs to migrate the content to another service.
- Use of Google search facility: Google is a well-established and profitable service, and its search facility is central to its service.
- Use of the Eventbrite on-line booking service: although further information about this company is not available, as it was used for informal purposes, its loss would not have been significant.
Applying A Risk Assessment Approach in an a Time of Economic Trouble
How should institutions respond in their uses of Web 2.0 services at a time of a global recession? Let us consider the economic risks to various stakeholder communities which may undermine the services provided by heritage organisations:
Externally-hosted Web 2.0 providers: What if the services provided by Google, Yahoo, etc. prove uneconomic and the services are shut down or the terms and conditions changed, with perhaps free-to-use services becoming subscription services?
Our institutions: What if the economic downturn affects the sustainability of the IT services provided within our institutions?
Our national services: What if the national services provided for our communities are similarly adversely affected, with users preferring the services provided by global services?
Our information providers: What if the services provided by individuals who use Slideshare, Flickr, etc. aren’t sustainable because the individuals face redundancy, early retirement, etc.?
Our funding organisations: What if our funding bodies have less money available, and are forced to stop or reduce the level of funding provided to national or institutional services?
Our user communities: What if our users’ expectations or interests change?
It should be clear that to dismiss externally-hosted services at a time of economic turmoil would be too simplistic an approach. Rather, there is a need to develop risk assessment and risk management approaches across a wide range of scenarios.
Risk assessment and accessibility
A holistic framework for Web accessibility is described by Kelly (2007) in which accessibility guidelines are treated as guidelines to be used when appropriate, and not as formal standards whose use is mandated. Further work (Kelly, 2008d) describes how this approach is particularly suited to a Web 2.0 environment in which content may be surfaced in a variety of environments (use of syndication technologies such as RSS, JavaScript widgets, etc.). This approach is based on the belief that universal accessibility is a false goal, as accessibility is dependent on complex issues such as the context and intended purpose of use, and not just the technical aspects of the Web resource itself. Rather than seeking universal access, the view is based on widening participation and social inclusion and seeking to ensure that the purpose of a service can be provided to the target audience.
More Answers: Shaping the Curve
The Gartner hype curve, a modified version of which is shown in Figure 1, provides a useful mechanism for understanding how new technologies may be perceived. This can help us to develop generic strategies which are appropriate at particular points on the curve when dealing with new technologies.
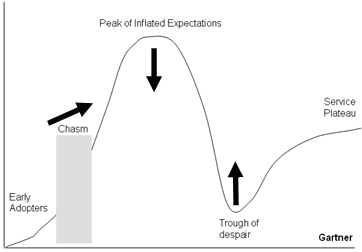
Fig 1: Gartner Hype Curve (modified)
Early adopters are the people who are technically savvy and are prepared to make do with (in fact, relish) beta versions which may be buggy, incomplete or inadequate in other ways. As the technology becomes more widespread, often with increased media coverage, it moves up the curve, before peaking at a point called the Peak of Inflated Expectations. Here media hype has expanded and extended the original reach of the technology to realms often way beyond those which are actually possible. Typically here we see the technology presented as somehow being a panacea.
At around this time, or earlier, voices of dissent begin to be heard. The technology isn’t as good as the hype. Shortly afterwards, the technology begins an inevitable descent into the trough of despair – before leveling out to the service plateau.
The technology chasm which is shown on the graph is often a critical time for any new technology. Given widespread understanding of how hype ebbs and flows, it is often during the rising phase that technology is at the highest risk of failing to gain a foothold in the mainstream. During this time, the challenges to organisations are at their most acute.
In order to avoid potentially useful technologies’ failure to bridge this chasm, and also to reduce the time it takes for useful technologies to move from use by early adopters to more widespread use, there is a need to adopt an appropriate set of strategies. Expectations as to the capabilities of a particular technology or the difficulties which may be experienced need to be realistic. Similarly there is a need to minimise the 'trough of despair' and to ease the transition to a stable service plateau – until, of course, the next disruptive technology arrives.
Avoiding the chasm
The following approaches may help to shape the Gartner hype in a Web 2.0 environment:
- Advocacy: It is not always true that IT innovation should be deployed in response to clearly articulated user requirements. The take-up of the Web in the early-to-mid 1990s was due to the potential which organisations identified once they had seen the Web and identified its potential to support current business requirements and to provide new services which hadn't been considered previously.
- Listening to and addressing concerns: Advocacy of the potential benefits should be followed up by a period of listening to concerns and addressing issues raised. There need not, however, be a clearly identified solution to all of the concerns. Solutions may emerge as more experience is gained. Alternatively, concerns may not be as significant as initially thought.
- Supporting enthusiasts: It is probably naive to expect everyone to be willing to accept a major new technological development. Rather than waiting to gain general acceptance, an alternative approach is to support those who are enthusiastic and who may still have concerns but would be willing to experiment.
- Refining approaches: It is important to ensure that the experiences (positive and negative) gained by the initial adopters are noted, and refinements to a final service deployment are developed.
- Doing a risk assessment: It may be a mistake to expect innovation to be completely risk free. Rather, any potential risks should be identified and assessed. There will be a balance between the risks associated with deploying an innovative service and the risks in doing nothing. The latter, for example, could be that one's competitors take the risks, and your organisation is marginalised.
- Managing expectations: The need to promote potential benefits in order to overcome inertia needs to be balanced against the need to avoid overselling the benefits of a technology or the effort needed to ensure that the technology is sustainable.
- Sharing experiences and expertise: Conferences and events (such as the Museums and the Web and the Museums and the Web UK conferences), mailing lists (such as the MCG JISCMail list) and resources (such as the UKOLN’s briefing documents) (UKOLN, 2008a) can help managers, policy makers developers and practitioners in learning about innovations and sharing implementation experiences.
Avoiding the Trough
Once technologies become over-hyped there is a danger that disillusionment will set in when the technologies fail to live up to expectations. The 'trough of despair' can be avoided by:
- Low risk and low cost solutions: In a Web 2.0 environment in particular, there may be low risk solutions which can be deployed for little cost. Hosted services such as Bloggers provide resilient, flexible, and most important, free means to build Web 2.0 platforms.
- Flexible business cases: At these early stages it can be useful to examine existing business models and reflect on the opportunities which new technologies may provide. For example, providing RSS feeds about the museum can allow third party aggregators to expose this information to their user community – which may result in visits to your physical museum from groups who might otherwise have proved difficult to reach.
- Quality assurance: There will be a need to develop and deploy quality assurance procedures which document both policies for the service and systematic procedures to ensure that the policies are being correctly implemented.
- Managed transition into a service environment: The enthusiasm innovators and early adopters may have is not likely to be sustainable when the innovation is deployed in a service environment. There will be a need to manage this transitional stage.
- Migration: The planning stage for the deployment of a new service should also be the time when plans are made for the migration of the service to a new environment. This should include the export of data held in the system as well as testing processes for importing the data into alternative services.
- Risk management: Migration of data is one aspect of a risk management strategy. A risk management strategy should also include aspects such as planning for server unavailability, dealing with performance problems, etc.
- Openness and Transparency: A simple technique for minimizing possible risks associated with innovation is to be open with one’s user community. If a new service is being trialed, inform the users of this, and be honest about possible dangers. You may find that users appreciate being informed and involved in the experimentation.
- Professional development: Ensure that those who are involved in the development work have suitable training. Also, ensure that other members of the organisation understand how Web 2.0 is being used and how possible risks are being managed.
A Framework for Exploiting The Benefits Of Web 2.0
The need for a framework
This paper has described various examples of best practices which seek to address the tensions between the benefits which Web 2.0 services may provide and associated risks and dangers. However, there is a need to describe a generic framework which can be used to assist the decision-making processes for a range of innovative Web 2.0 services.
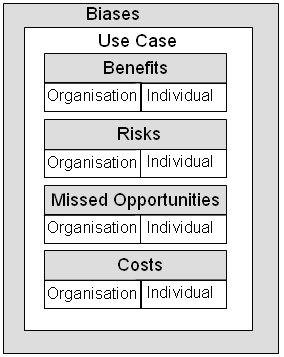
Fig 2: Framework for Exploiting Web 2.0
The framework is illustrated in Figure 2. It is based on seeking to reconcile possible tensions between the two main stakeholders: the institution and the user.
The following components for the framework are used:
- Benefits: A description of the benefits for the organisation and for the user.
- Risks: A description of the risks for the organisation and for the user.
- Missed opportunities: A description of the missed opportunities and benefits for the organisation and for the user if the service is not used.
- Costs: A description of the costs and resource implications associated with use of the organisation and for the user.
In addition, define the particular use cases or intended purposes which are envisaged for the service. This is to acknowledge that there will be personal and organisational biases and other subjective factors when using the framework.
Applying The Framework 1: Use of Twitter
Let us explore how this framework can be used by applying it in a number of different contexts. The first example considers the factors an institution needs to consider when considering making use of the Twitter micro-blogging service.
- Intended purpose: Marketing of museum events and other activities.
- Benefits (institution): There are no licensing costs. Content creation costs will be low due to limited size of content. Will be able to see ‘followers’ and potentially contact them directly. In US/Canada content can be delivered for free via SMS.
- Benefits (user): The end user (recipient) will be able to receive brief snippets of news from the museum without having to establish a ‘friend’ relationship as is the case in many social networking services. In US/Canada, content can be received for free via SMS.
- Risks (institution): The Twitter service is known to be unreliable, with content not always delivered in a timely fashion. The longer-term sustainability model for Twitter is uncertain. Not everyone will use or wish to use Twitter.
- Risks (user): There would appear to be little risk for the end user, but if the user relies on delivery of Twitter messages, this may cause problems if the quality of the service deteriorates.
- Missed opportunities (institution): Examination of uses made by various other museums illustrates possible benefits. Twitter may also provide a simple mechanism for providing content for delivery to mobile devices (e.g. iPhones) without having to initiative development work. There may also be dangers that a Twitter ID associated with an institution is claimed by others.
- Missed opportunities (user): The end users would miss out on the opportunity to receive information from institutions they may wish to develop links with.
- Costs (institution): Low cost for simple usage. More effort may be needed if backend systems are needed to automate production and archiving of Twitter posts, although such additional development work tends not to be the norm currently.
- Costs (user): As the numbers of Twitter users increases, the usefulness of the service may deteriorate.
- Biases & other subjective issues: Some Twitter users regard Twitter as primarily for building communities and connections, not marketing.
Let us now look at a second potential use of Twitter.
- Intended purpose: To support community building and link with other museum professionals outside the institution.
- Benefits (institution): The institution can gain from better informed staff.
- Benefits (user): One of Twitter’s key areas of usage is by early adopters in the development community. Providing a supportive framework which encourages developers to explore the potential of Twitter for engagement with peers may result in productivity gains and support professional development.
- Risks (institution): Inappropriate Twitter posts could reflect badly on the organisation. The organisation may wish to keep close control over the management of its reputation. There may be dangers that time spent in using Twitter fails to deliver an adequate return on investment.
- Risks (user): Use of Twitter may not be suited to everyone. Staff may feel alienated if they feel forced into use of Twitter.
- Missed opportunities (institution): Not particularly applicable.
- Missed opportunities (user): The user who may be prevented from using Twitter as a mechanism for collaboration and community support may lose these benefits and feel resentment. The user who chooses not to use the tool may miss out on a potentially useful tool.
- Costs (institution): Costs in staff time.
- Costs (user): As the numbers of Twitter users increases, the usefulness of the service may deteriorate.
- Biases & other subjective issues: Use of Twitter may not reflect a user’s preferred style of working.
It should be noted that to avoid the dangers of conflating several different intended purposes, which may have conflicting benefits and risks, the framework is applied for each distinct use case.
Conclusions
This paper has argued that the museum community needs to complement its initial experimentation with Web 2.0 with the development of approaches which identify potential risks and seek to manage (rather than eliminate) such risks. A framework being developed to support the management of such approaches has been described. Chances of its success will be increased by input from practitioners across the museum sector. We welcome feedback and comments and invite readers to give their comments on UKOLN’s blog for the cultural heritage sector (http://blogs.ukoln.ac.uk/cultural-heritage/).
References
Adie,C. (2008). “Web 2.0: Managing the risks”. Eduserv Symposium 2008. http://www.eduserv.org.uk/foundation/symposium/2008/presentations/chrisadie (Accessed 27 January 2009).
Bernstein, S. (2008). “Where Do We Go From Here? Continuing with Web 2.0.” In Museums and the Web 2008: Proceedings. Toronto: Archives & Museum Informatics. (Ed. J. Trant and D. Bearman). http://www.archimuse.com/mw2008/papers/bernstein/bernstein.html (Accessed 27 January 2009).
Caruth, N. & S. Bernstein (2007). “Building an On-line Community at the Brooklyn Museum: A Timeline”, In Museums and the Web 2007: Proceedings (Ed. J. Trant and D. Bearman). Toronto: Archives & Museum Informatics. http://www.archimuse.com/mw2007/papers/caruth/caruth.html (Accessed 27 January 2009)
Chan, S. & J. Spadaccini (2007). “Radical Trust: The State of the Museum Blogosphere.” In Museums and the Web 2007: Proceedings. Toronto: Archives & Museum Informatics (Ed. J. Trant and D. Bearman). http://www.archimuse.com/mw2007/papers/spadaccini/spadaccini.html (Accessed 27 January 2009).
Edinburgh (2007). “Guidelines for using external services”. University of Edinburgh. https://www.wiki.ed.ac.uk/display/Web2wiki/Web+2.0+Guidelines (Accessed 27 January 2009).
Ellis,M. (2008) ”Introducing Onetag”. MW2008 blog, 24 Mar 2008. http://conference.archimuse.com/blog/dmje/introducing_onetag (Accessed 27 January 2009).
JISC PoWR (2008a) The JISC PoWR Blog, http://jiscpowr.jiscinvolve.org/. (Accessed 27 January 2009).
JISC PoWR (2008b). JISC PoWR Preservation Handbook. The JISC PoWR Blog, http://jiscpowr.jiscinvolve.org/handbook/ (Accessed 27 January 2009).
Kelly,B., E. Tonkin and P. Shabajee (2005). “Using Networked Technologies To Support Conferences”. , EUNIS 2005, June 2005. http://www.ukoln.ac.uk/web-focus/papers/eunis-2005/paper-1/. (Accessed 27 January 2009).
Kelly, B., D. Sloan, S. Brown, J. Seale, H. Petrie, P. Lauke, and S. Ball, (2007). “Accessibility 2.0: People, Policies and Processes”. WWW 2007 Banff, Canada, 7-11 May 2007. http://www.ukoln.ac.uk/web-focus/papers/w4a-2007/ (Accessed 27 January 2009)
Kelly, B. (2008a). “Squirl: When Web 2.0 Services Break”. UK Web Focus blog, 25 Aug 2008. http://ukwebfocus.wordpress.com/2008/08/25/squirl-when-web-20-services-break/ (Accessed 27 January 2009).
Kelly, B. (2008b). “What Can the Social Web Offer The Heritage Sector?” ASVA 2008 Conference, 14 November 2008, UKOLN. http://www.ukoln.ac.uk/cultural-heritage/events/asva-2008/ (Accessed 27 January 2009).
Kelly, B. (2008c). “How Rude! Use Of WiFi Networks At Conferences”. UK Web Focus blog, 12 May 2008. http://ukwebfocus.wordpress.com/2008/05/12/how-rude-use-of-wifi-networks-at-conferences/ (Accessed 27 January 2009).
Kelly, B., L. Nevile, EA. Draffan and S. Fanou (2008d). “One World, One Web ... But Great Diversity”. WWW 2008 Beijing, China, 21-22 April 2008. http://www.ukoln.ac.uk/web-focus/papers/w4a-2008/ (Accessed 27 January 2009).
Simon, N. Museum 2.0 (2008a). “What is Twitter, Really? And Can It Do Anything For Museums?” Museum 2.0 blog, 16 April 2008. http://museumtwo.blogspot.com/2007/04/what-is-twitter-really-and-can-it-do.html (Accessed 27 January 2009).
Simon, N. (2008b). Museum 2.0 blog, 30 December 2008. http://museumtwo.blogspot.com/2008/12/open-letter-to-museums-on-twitter.html (Accessed 27 January 2009).
O’Reilly, T. (2005). “What Is Web 2.0?” http://www.oreillynet.com/pub/a/oreilly/tim/news/2005/09/30/what-is-web-20.html (Accessed 27 January 2009).
Powell, A (2007). JISC CETIS conference - day 1. eFoundations blog, 21 November 2007. http://efoundations.typepad.com/efoundations/2007/11/jisc-cetis-conf.html (Accessed 27 January 2009).
Sloan, D., Kelly, B., Heath, A., Petrie, H. Fraser, H. and Phipps, L. (2006). “Contextual Web Accessibility - Maximizing the Benefit of Accessibility Guidelines”. WWW2006 Edinburgh, Scotland 22-26 May 2006. http://www.ukoln.ac.uk/web-focus/papers/w4a-2006/ (Accessed 27 January 2009).
Twittergroups (nd) “Twitter Groups: Museums”. http://twittgroups.com/group/museums (Accessed 27 January 2009).
UKOLN (2008a). “Sharing Made Simple Workshop: Copy of Event Wiki” UKOLN. http://www.ukoln.ac.uk/cultural-heritage/events/sharing-made-simple-20080910/wiki/ (Accessed 27 January 2009).
UKOLN (2008b). “MLA Yorkshire Workshop:Workshop Feedback”. UKOLN. http://www.ukoln.ac.uk/web-focus/events/workshops/mla-yorkshire-2008-05/feedback (Accessed 27 January 2009).
UKOLN (2008c). “MLA Yorkshire Workshop. 12 May 2008” UKOLN. http://www.ukoln.ac.uk/web-focus/events/workshops/mla-yorkshire-2008-05/ (Accessed 27 January 2009).
UKOLN (2008d). “MLA London Workshop, 14 July 2008”. UKOLN. http://www.ukoln.ac.uk/cultural-heritage/events/mla-london-2008-07/ (Accessed 27 January 2009.
UKOLN (2008e). “CyMAL Workshop, 10 September 2008”. UKOLN. http://www.ukoln.ac.uk/cultural-heritage/events/sharing-made-simple-20080910/ (Accessed 27 January 2009).
UKOLN (2008f). ”UKOLN IntroBytes”. UKOLN. http://www.ukoln.ac.uk/cultural-heritage/documents/ (Accessed 27 January 2009).
UKOLN (2008g). “Risk Assessment for IWMW 2008 Web Site”. UKOLN. http://www.ukoln.ac.uk/web-focus/events/workshops/webmaster-2008/risk-assessment/ (Accessed 27 January 2009).
Weller, M. (2008). “Making Connections 2.0”. Ed Techie Blog, 2 May 2008. http://nogoodreason.typepad.co.uk/no_good_reason/2008/05/making-connecti.html (Accessed 27 January 2009).
Wikipedia (2008). “Amplified Conferences”. Wikipedia. http://en.wikipedia.org/wiki/Amplified_conference (Accessed 27 January 2009).
